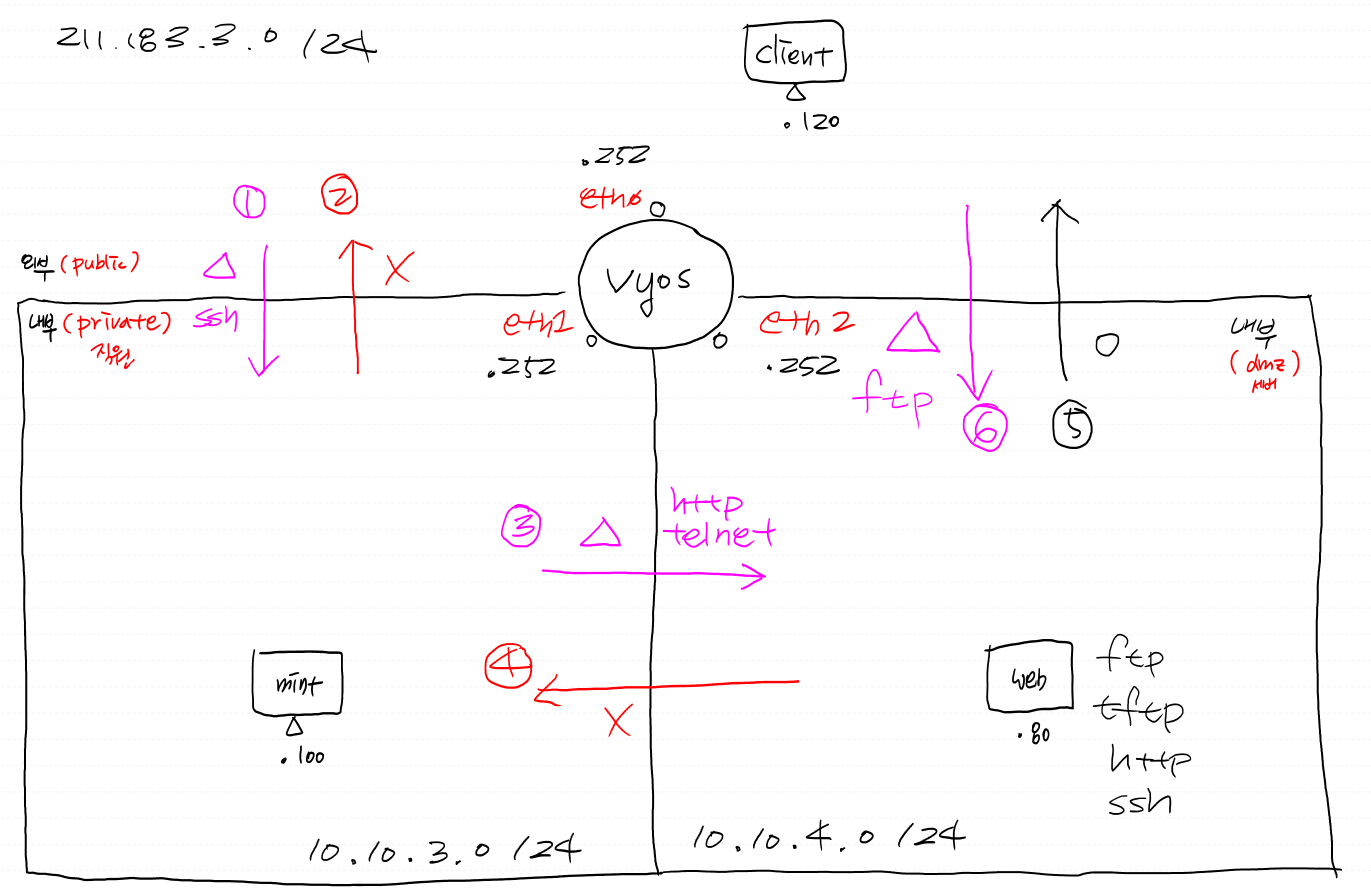
문제)
기존 VyOS는 서스펜드 해두시고 VyOS-exam을 만드셔서 아래와 같이 구성해보세요. 사전에 잘 되는것을 확인한 스샷과 1,2,3,4,5,6을 각각 구성한 후의 스샷을 엮어서 제출하세요.
- eth0 설정
vyos@vyos# set system gateway-address 211.183.3.2
vyos@vyos# set service ssh port 222
vyos@vyos# set int eth eth0 add 211.183.3.252/24
vyos@vyos# commit
- NIC(vmnet3) 추가 후 eth1 설정
vyos@vyos# set int eth eth1 add 10.10.3.252/24
vyos@vyos# commit
- NIC(vmnet4) 추가 후 eth2 설정
vyos@vyos# set int eth eth2 add 10.10.4.252/24
vyos@vyos# commit


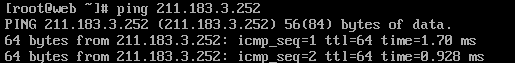
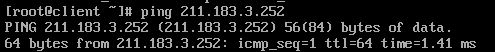
NAT 설정
- 웹서버에서 설치해야하는 서버
ssh, ftp, telnet, httpd
- web서버에 2222번으로 ssh 접속되도록 DNAT 설정
vyos@vyos# set nat destination rule 100 destination port 2222
vyos@vyos# set nat destination rule 100 inbound-interface eth0
vyos@vyos# set nat destination rule 100 translation add 10.10.4.80
vyos@vyos# set nat destination rule 100 translation port 22
vyos@vyos# set nat destination rule 100 protocol tcp
- mint서버에 22번으로 ssh 접속되도록 DNAT 설정
vyos@vyos# set nat destination rule 200 destination port 22
vyos@vyos# set nat destination rule 200 inbound-interface eth0
vyos@vyos# set nat destination rule 200 protocol tcp
vyos@vyos# set nat destination rule 200 translation address 10.10.3.100

- web에서 외부로 통신하기 위해 PAT 설정
vyos@vyos# set nat source rule 100 outbound-interface eth0
vyos@vyos# set nat source rule 100 source address 10.10.0.0/21
# GNS3의 overload와 동일한 옵션
vyos@vyos# set nat source rule 100 translation add masquerade
vyos@vyos# commit


ftp, telnet, http
[root@web ~]# yum install -y vsftpd telnet-server httpd
[root@web ~]# systemctl restart telnet.socket vsftpd httpd
- 테스트 파일 생성
[root@web ~]# echo ftp-test > /var/ftp/test.txt
- ftp를 위한 DNAT 설정
vyos@vyos# set nat destination rule 300 destination port 20,21
vyos@vyos# set nat destination rule 300 inbound-interface eth0
vyos@vyos# set nat destination rule 300 protocol tcp
vyos@vyos# set nat destination rule 300 translation add 10.10.4.80
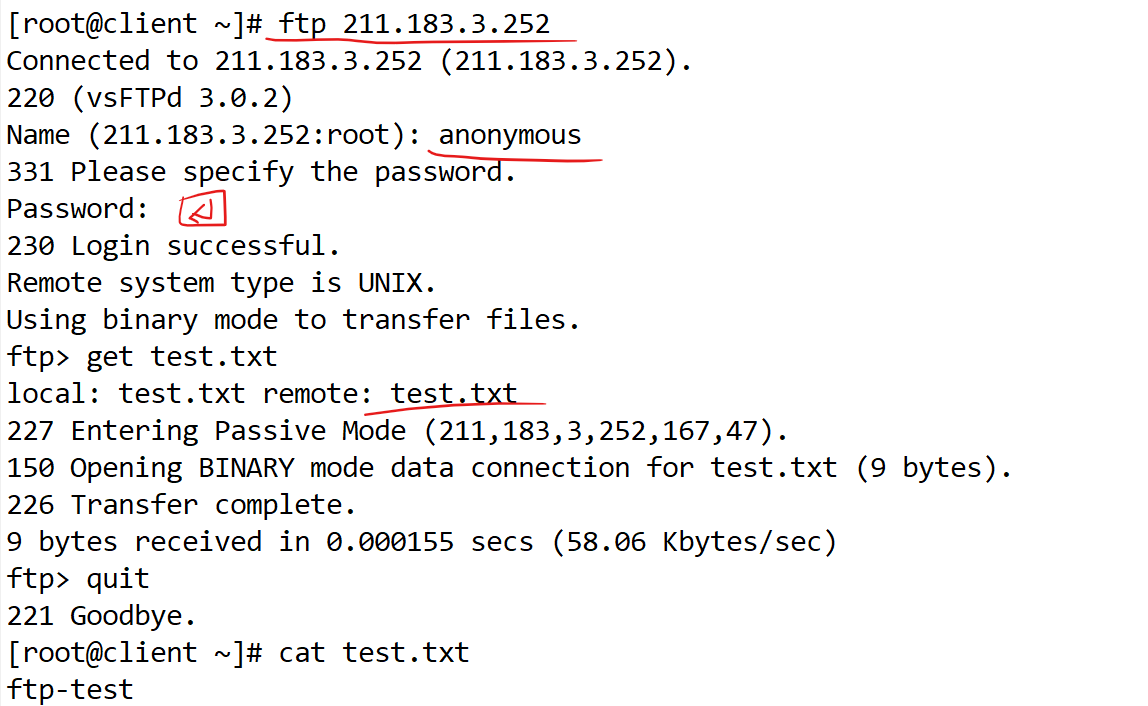
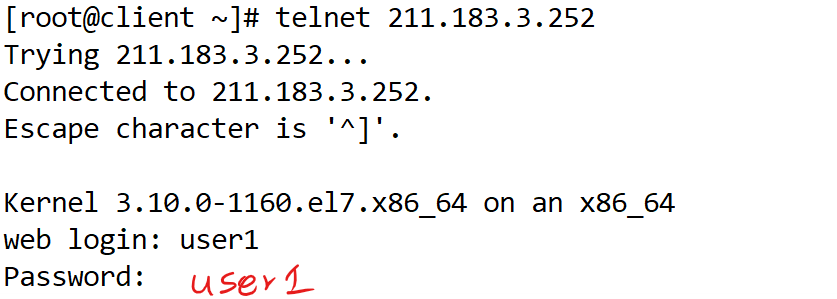
[root@client ~]# yum install -y telnet
# 혹시 모르니 텔넷도 해보자
- 나중에 테스트 용도로 사용 예정
vyos@vyos# set nat destination rule 400 destination port 23
vyos@vyos# set nat destination rule 400 inbound-interface eth0
vyos@vyos# set nat destination rule 400 protocol tcp
vyos@vyos# set nat destination rule 400 translation add 10.10.4.80
vyos@vyos# commit

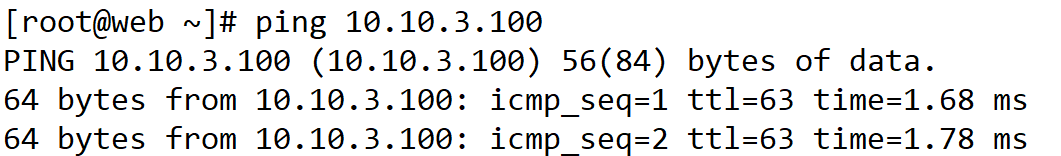


→ 전체 영역이 서로 통신이 잘 되는걸 확인함
방화벽 설정
- 존설정
vyos@vyos# set zone-policy zone public int eth0
vyos@vyos# set zone-policy zone private int eth1
vyos@vyos# set zone-policy zone dmz int eth2

# 존 설정 이후에 모든 통신이 안되는걸 확인. + web이나 mint로 xshell 접속이 다 끊김
- 1번 설정
# 정책 설정
vyos@vyos# set firewall name PUBLIC_TO_PRIVATE rule 10 action accept
vyos@vyos# set firewall name PUBLIC_TO_PRIVATE rule 10 protocol tcp
vyos@vyos# set firewall name PUBLIC_TO_PRIVATE rule 10 destination port 22
# 정책 적용
vyos@vyos# set zone-policy zone private from public firewall name PUBLIC_TO_PRIVATE
- 2번 설정
# 정책 설정
vyos@vyos# set firewall name PRIVATE_TO_PUBLIC rule 20 action accept
vyos@vyos# set firewall name PRIVATE_TO_PUBLIC rule 20 protocol all
vyos@vyos# set firewall name PRIVATE_TO_PUBLIC rule 20 state established enable
vyos@vyos# set firewall name PRIVATE_TO_PUBLIC rule 20 state related enable
# 정책 적용
vyos@vyos# set zone-policy zone public from private firewall name PRIVATE_TO_PUBLIC

- 3번 정책 설정
# 정책 생성
vyos@vyos# set firewall name PRIVATE_TO_DMZ rule 30 action accept
vyos@vyos# set firewall name PRIVATE_TO_DMZ rule 30 protocol tcp
vyos@vyos# set firewall name PRIVATE_TO_DMZ rule 30 destination port 80,23
# 정책 적용
vyos@vyos# set zone-policy zone dmz from private firewall name PRIVATE_TO_DMZ
- 4번 정책 설정
# 정책 생성
vyos@vyos# set firewall name DMZ_TO_PRIVATE rule 40 action accept
vyos@vyos# set firewall name DMZ_TO_PRIVATE rule 40 protocol all
vyos@vyos# set firewall name DMZ_TO_PRIVATE rule 40 state established enable
vyos@vyos# set firewall name DMZ_TO_PRIVATE rule 40 state related enable
# 정책 적용
vyos@vyos# set zone-policy zone private from dmz firewall name DMZ_TO_PRIVATE
vyos@vyos# commit
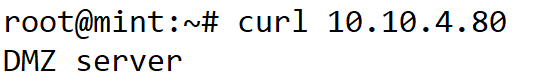

# mint에서 web으로 telnet 확인
- 5번 정책
# 정책 생성
vyos@vyos# set firewall name DMZ_TO_PUBLIC rule 50 action accept
# 정책 적용
vyos@vyos# set zone-policy zone public from dmz firewall name DMZ_TO_PUBLIC
- 6번 정책
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 60 action accept
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 60 protocol tcp
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 60 destination port 20,21
# 퍼블릭에서 dmz로 가는 ftp 트래픽을 위한 설정
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 61 action accept
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 61 protocol all
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 61 state established enable
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 61 state related enable
# 61번 rule은 오로지 5번 정책을 위한 rule이다.
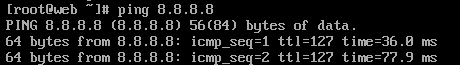

# 민트로는 당연히 통신이 안된다.

문제)
호성이는 VyOS를 통해 다양한 서버를 운영하고자 한다.
주어진 내부 대역은 10.20.30.0 /23 대역이며 vmnet5, 6을 사용한다. VAR과 DB라는 두개의 내부 Zone과 PUB zone을 통해 다음과 같은 구성을 하고자한다.
→ 10.20.30.0 /24 , 10.20.31.0 /24
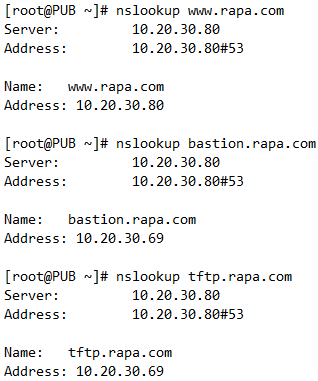
1. VAR zone에 varwp라는 호스트네임을 갖는 wordpress 서버를 구성하고, DB zone에는 dbdb라는 이름의 mariadb 데이터베이스 서버 구성을 하고자한다. wordpress 서비스는 PUB 대역에 제공하며 사용자들은 www.rapa.com으로 접속해야한다.
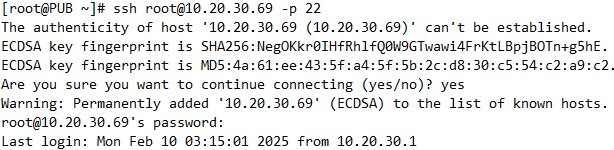
2. 재택근무중인 태호 사원은 데이터베이스 관리자이며, VAR zone의 bastion이라는 호스트네임을 갖는 서버에 bastion.rapa.com이라는 영문주소로 ssh 접속이 가능하며, 이 서버를 경유하여 DB zone의 dbdb 서버에 ssh로 접속하여야 한다. DB서버는 절대 PUB zone에서의 접속을 허용하지 않는다.
3. bastion 서버는 PUB 대역에 tftp 서비스도 제공한다. 사용자들은 tftp.rapa.com으로 이 서버에 접속할 수 있다.
주의) firwall-cmd로 방화벽 열어줄때 --add-service=tftp, --add-port=69 양쪽 다 열어주세요.
이때 서버의 방화벽은 물론, ZONE기반 방화벽 정책 구성을 통해 반드시 필요한 트래픽만 허용해야한다.
| client | |||
| PUB 211.183.3.120 211.183.3.0 /24 (vmnet8) |
|||
| ↑ (X) / ↓(△ http, ssh, tftp, dns) | .250 .250 VyOS .250 |
↑ (X) / ↓(X) | |
| VAR varwp: wordpress, dns 10.20.30.80 bastion: ssh, tftp 10.20.30.69 10.20.30.0 /24 (vmnet5) |
← (X) → (db, ssh) |
DB mariadb(dbdb) 10.20.31.33 10.20.31.0 /24 (vmnet6) |
|
NAT 설정
- VAR서버에서 설치해야하는 서버
ssh, tftp, httpd
- db서버에 2222번으로 ssh 접속되도록 DNAT 설정
vyos@vyos# set nat destination rule 100 destination port 2222
vyos@vyos# set nat destination rule 100 inbound-interface eth0
vyos@vyos# set nat destination rule 100 translation add 10.20.31.33
vyos@vyos# set nat destination rule 100 translation port 22
vyos@vyos# set nat destination rule 100 protocol tcp
- varwp서버에 222번으로 ssh 접속되도록 DNAT 설정
vyos@vyos# set nat destination rule 200 destination port 22
vyos@vyos# set nat destination rule 200 inbound-interface eth0
vyos@vyos# set nat destination rule 200 protocol tcp
vyos@vyos# set nat destination rule 200 translation port 22
vyos@vyos# set nat destination rule 200 translation address 10.20.30.80
- varwp에서 외부로 통신하기 위해 PAT 설정
vyos@vyos# set nat source rule 200 outbound-interface eth0
vyos@vyos# set nat source rule 200 source address 10.20.30.0/23
# 10.20.0.0/19
# GNS3의 overload와 동일한 옵션
vyos@vyos# set nat source rule 200 translation add masquerade
vyos@vyos# commit
- tftp를 위한 DNAT 설정
vyos@vyos# set nat destination rule 300 destination port 69
vyos@vyos# set nat destination rule 300 protocol udp
vyos@vyos# set nat destination rule 300 inbound-interface eth0
vyos@vyos# set nat destination rule 300 translation address 10.20.30.80
vyos@vyos# set nat destination rule 300 translation port 69
vyos@vyos# commit
ssh, tftp, http, wp
[root@web ~]# yum install -y tftp httpd
[root@web ~]# systemctl restart telnet.socket vsftpd httpd

- 테스트 파일 생성
[root@web ~]# echo ftp-test > /var/ftp/test.txt

- decription 설정
vyos@vyos# set int eth eth0 description pub
vyos@vyos# set int eth eth1 description var
vyos@vyos# set int eth eth2 description db
vyos@vyos# commit
VyOS Firewall
- private, public, dmz 각 존을 설정
vyos@vyos# set zone-policy zone pub interface eth0
vyos@vyos# set zone-policy zone var interface eth1
vyos@vyos# set zone-policy zone db interface eth2
vyos@vyos# commit
| client | |||
| PUB 211.183.3.120 211.183.3.0 /24 (vmnet8) |
|||
| ↑(X) / ↓(△ http, ssh, tftp, dns) | .250 .250 VyOS .250 |
↑ (X) / ↓(X) | |
| VAR varwp: wordpress, dns 10.20.30.80 bastion: ssh, tftp 10.20.30.69 10.20.30.0 /24 (vmnet5) |
← (X) → (db, ssh) |
DB mariadb(dbdb) 10.20.31.33 10.20.31.0 /24 (vmnet6) |
|
1. 정책10 ↓(△ http, ssh, tftp, dns)
tcp: http(80), ssh(22), dns(53)
udp: tftp(69), dns(53)
vyos@vyos# set firewall name PUB_TO_VAR rule 10 action accept
vyos@vyos# set firewall name PUB_TO_VAR rule 10 protocol tcp
vyos@vyos# set firewall name PUB_TO_VAR rule 10 destination port 22,53,80
vyos@vyos# set firewall name PUB_TO_VAR rule 15 action accept
vyos@vyos# set firewall name PUB_TO_VAR rule 15 protocol udp
vyos@vyos# set firewall name PUB_TO_VAR rule 15 destination port 53,69
vyos@vyos# set zone-policy zone var from pub firewall name PUB_TO_VAR
vyos@vyos# commit

2. 정책20 ↑(X)
vyos@vyos# set firewall name VAR_TO_PUB rule 20 action accept
vyos@vyos# set firewall name VAR_TO_PUB rule 20 state established enable
vyos@vyos# set firewall name VAR_TO_PUB rule 20 state related enable
vyos@vyos# set firewall name VAR_TO_PUB rule 20 protocol all
vyos@vyos# set zone-policy zone pub from var firewall name VAR_TO_PUB
vyos@vyos# commit
3. 정책30 →(db, ssh)
tcp: db(3306), ssh(22)
vyos@vyos# set firewall name VAR_TO_DB rule 30 action accept
vyos@vyos# set firewall name VAR_TO_DB rule 30 protocol tcp
vyos@vyos# set firewall name VAR_TO_DB rule 30 destination port 22,3306
vyos@vyos# set zone-policy zone db from var firewall name VAR_TO_DB
vyos@vyos# commit
4. 정책40 ←(X)
vyos@vyos# set firewall name DB_TO_VAR rule 40 action accept
vyos@vyos# set firewall name DB_TO_VAR rule 40 state established enable
vyos@vyos# set firewall name DB_TO_VAR rule 40 state related enable
vyos@vyos# set firewall name DB_TO_VAR rule 40 protocol all
vyos@vyos# set zone-policy zone db from var firewall name DB_TO_VAR
vyos@vyos# commit
'AWS Cloud School 8기 > VyOS' 카테고리의 다른 글
| 28일차) 2025-02-07 (VyOS+http/tftp/ssh) (0) | 2025.02.07 |
|---|---|
| 27일차) 2025-02-06 (VyOS 초기설정) (0) | 2025.02.06 |